Once started, you will be presented with the following GUI screen: Without a Host header, each web site would have to have a unique IP address. To impact a somewhat important companies infrastructure the attack will need at least 65GB or higher The attacks on the websites of the Justice Department and others in the wake of the takedown of Megaupload. While the request header names and payloads, in and of themselves, are valid, the order in which they are defined in the request do not match what normal web browsers would send. Sep 26, Digital Canaries in a Coal Mine: 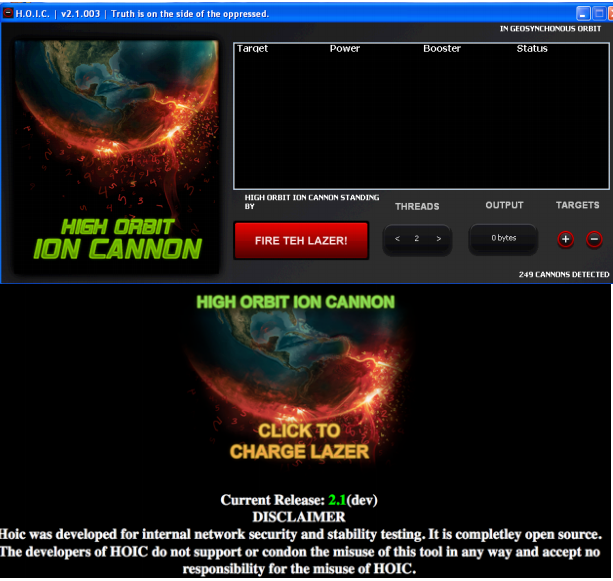
| Uploader: | Bara |
| Date Added: | 5 November 2009 |
| File Size: | 57.99 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 71712 |
| Price: | Free* [*Free Regsitration Required] |
In saying all that, if you were to pen test am individual at a home PC the bandwidth needed will not be as much.

Michal Zalewski recently updated his Passive OS Finferprinting p0s tool to v3 which includes application layer fingerprinting capabilities. Before we discuss some of the unique identifiers of HOIC traffic, we wanted to make sure to highlight the generic detection of automated DoS detection through traffic velocity violations.
They usually do this by either overwhelming one or more of the resources of the server that hosts the website or application with traffic, or by disrupting a network service that the server depends on.
But as the group has engaged in increasingly high-profile attacks on government and corporate websites, doing so effectively and staying out of harm's way have become an ever-growing challenge.
By examining the valid header ordering shown here in p0f3, we can identify that the HOIC header ordering is abnormal. Scriot started, you will be presented with the following GUI screen:.

The script also can include a randomized list of user agents, referring sites and random headers that are fed into HTTP requests to make the requests look more legitimate:.
In addition to the GenericBoost. While it does make detection more difficult, it is still possible. Recently, the SANS Internet Storm Center ISC also highlighted a javascript verion of LOIC that, while generating the same attack traffic as our previous analysis showed, actually executed the attacks without the user "initiating" the attacks by pressing any buttons. Recent SpiderLabs Blog Posts. Attack description Widespread HOIC availability means that users having limited knowledge and experience can execute potentially significant DDoS attacks.
HOIC isn't exactly rocket science. Read complimentary reports and insightful stories in the Trustwave Resource Center. While it seems that most of the dowload links have been removed by law enforcement agencies, we were able to obtain a copy and have conduct dynamic analysis on it.
High Orbits and Slowlorises: understanding the Anonymous attack tools
One script is specifically targeting a government web site in retaliation for prosecuting someone for using LOIC is previous attacks. In this screenshot, we are highlighting the Keep-Alive field.

By boster to use this site you are agreeing to our use of cookies. The user can control the number of threads used per attack. Since renting a large botnet can be expensive and unwieldy, attackers typically look for additional ways to amplify the size of their attacks, one such amplification technique called DNS reflection.
By providing my information and clicking on the register button, I confirm that I have read and agree to this website's terms and conditions and privacy policy. Failing to do so will result in your account being terminated.
What makes ddos so cool or scary in first understanding the attack bu useing usch binaries of HOIC is the fact that one can designate a target and click a button and then witness the TTL dwindle to a stop The Host header's main purpose was to help conserve IP address space by allowing name-based virtual hosting. Most of these tell-tale signs are based on abnormalities boic.
High Orbits and Slowlorises: understanding the Anonymous attack tools | Ars Technica
While some in the group continued to try hojc get enthusiastic followers or unwary webpage visitors to use a Web browser version of the Low Orbit Ion Cannon attack tool, use of LOIC had led to the arrests of members of Anonymous and LulzSec last summer. SendAttack is pretty straightforward:.
Attackers are constantly changing their tactics and tools in response to defender's actions. These rules will initiate the drop action on all traffic from the attacker source and will provide periodic alerting with traffic stat counts. With the default settings shown above, the HTTP requests look like this:.
free botnet comment for password: Tools Ddos HOIC v
While the request header names and payloads, in and of themselves, are valid, the order in which they are defined in the request do not match what normal web browsers would send. There is no internet connection required. Notice that after the Header Name and semi-colon, that there is actually two space characters 20 20 before the payload text in the hex scfipt. In latemembers of Anonymous began to step away from their most well-known weapon for distributed denial of service attacks.
The only limitation with this dataset is that it is quite old.

No comments:
Post a Comment